
Holistic Cybersecurity and ExO
The article features a new approach to cybersecurity and the top ten cybersecurity recommendations. Included is an example of how they apply to the ExO Attributes.
This article extracts highlights from a book written to address large areas missing in cybersecurity defenses that can put an organization at risk and that are only revealed when you look at security holistically.
The world has changed since ExO Methodology was created. Today Cybersecurity has become a top-of-mind conversation, and in turn, ExO is imperative in introducing Cybersecurity across the organization. This article explores both as a new contribution to the ExO community and a new approach to Cybersecurity.
Motivation
Most Cybersecurity services and products focus on the IT department, selling “complete” branded solutions or "Complete Zero Trust Solutions" yet missing critical actions, leaving many weak links that can impact the entire organization.
Well, frankly, that just doesn’t cut it - and I felt it was time to set the record straight.

My new book, A Holistic Approach To Cybersecurity, covers all aspects of organizations, small & large, starting critically with the executive team. It includes the now distributed workforce, suppliers, and contractors of all kinds. It looks at long-term causes and covers the latest IT innovations and Zero Trust strategies. It alerts you to the latest scary threats and their impact.
I wrote the book for those executives who have neither the time nor inclination to read it! Why? Well, because if it's not understood or adopted by the organization’s leadership, it will likely fail - and the organization will remain at risk. If this sounds like a familiar ExO discussion to you, then it does to me too – and it’s really what triggered the idea and the synergy between implementing holistic cybersecurity and ExO based transformation. The article is also expressed for the ExO audience of consultants and advisors who need to encompass the topic with their clients.
Oh. yes, the title: “Hey, who left the back door open? The strength of the front door doesn’t matter if the back doors are left open. In today’s Cloud-oriented, distributed workforce world, there are no walls, let alone back doors to defend - and the enemy is likely already inside!
I have run my own strategic marketing company for the last 16 years, and in 2019, I met Salim and Kent and was hooked on ExO, became a certified consultant and sprint coach, and ExO thinking influences all my work. I should mention that for the last several decades, I've worked in software, testing, and security in development, marketing, and sales and chaired several international network standards bodies.
Scope and Strategy
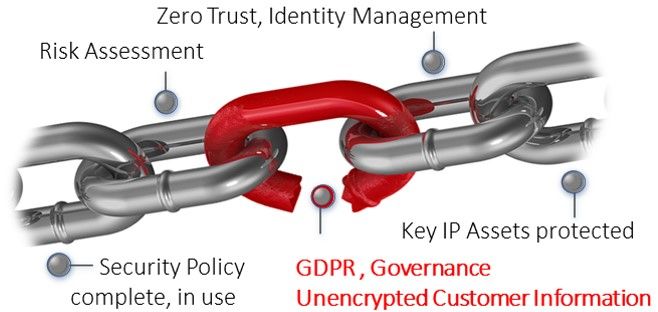
The scope and strategy encompass all areas. This translates into actions covering: management commitment & policies, HR, hiring, least privilege, insider threats, distributed workforce, legal & governance, DevSecOps, supply chain, physical security, operations, sales, marketing, R&D, hybrid cloud, finance, legal, accountability, and monitoring across all departments. IT's role covers automation, asset curation and risk assessment, and real understanding of Zero trust. This article gives you ten themes to focus on.
The book has something for everyone. For the person responsible for cybersecurity, it’s a checklist of what’s needed to implement Holistic Cybersecurity. If you are not part of the executive team or don’t have dedicated security or IT resource, its structure - shown here- shapes the guidance on what to do and what to delegate.
As we know, any disruptive technology or shift in an organization’s established practices encounters the organization's immune system. A holistic approach to cybersecurity is no exception, as it requires technology and organizational shift. Then, talking with Kent, I discovered that the topic of Cybersecurity was yet another reason to resist any shift to implementing the ExO methodology. So why not combine the two?
For ExO, the big challenge is the lack of cybersecurity overlay to the attributes. Putting the two together creates a big opportunity. The book gives you the "language" to empower your discussions and to be a contributer, and to accelerate implementation.
Security Overlay to the ExO Attributes

This is a conversation that will be specific to each client/customer. For example, "Leveraged Assets" may mean interfacing with third-party systems that can create privacy exploits recently in the airline & hotel businesses. Smaller organizations may not be aware of some of the concerns, so this will be an opportunity to use the work to your advantage
The Top Ten Recommendations
I'm not sure why we like top ten lists. (The book has over 100 actions) Anyway, I selected these as my top ten Cybersecurity recommendations:
1 Adopt a Holistic Approach by the executive team led by the CSO
• Have & implement a security policy and strategy
2 Use the guidance of the book to cover all aspects of the organization
• HR: Focus on people, establish least privilege access, address insider threats
• Train everyone to avoid phishing attacks. Legal, Governance, Privacy, etc.
• Study the ExO attributes to see where you can see the impact of Cybersecurity
3 Curate your assets.
• Assess risks v cost to defend them
• Safeguard assets from phishing attacks, data breaches and more
4 Understand the cause and ongoing impact of cybercrime
• The shift to the Cloud eliminated defense of the network perimeter
• Covid-accelerated, distributed workforces, supply chains and open source
• State-sponsored cyber attacks exploited and shattered network defense
5 Adopt Zero Trust - critical for the perimeter-less network
• Identity, authentication, access control, policy enforcement
• Identify critical points to implement
• Don't trust, verify - with time-sensitive automated monitoring
6 Delegate – don’t abdicate. Be responsible, your business depends on it
• Oversee Staff, suppliers, secure hybrid cloud providers, etc.
• Oversee all providers, supply chain, open source suppliers, all outsiders
7 Strengthen every weak link, to deflect not defend
• Use the book's guidance to address the 100+ actions covered
8 Automate to eliminate people issues, scale, monitor and report
9 Be threat-aware & technology-aware to understand the 100+ topics
10 Concentrate: you’re never done, Cybersecurity threats change daily
Epilogue, What's next?
Well, this was just intended as a beginning, and I hope it gave you a flavor of this massive topic. The book is packed with information and it’s not just informative – it’s Transformative - giving guidance in the form of a Playbook of 100 actions in the mind-bending world of Cybersecurity that moves faster than you can read about it.
Speaking of reading about it, the full book is available on Amazon. Check out my blog on Zero Trust and my recent panel video blog on security in the network cloud. Better still, contact me in the ExO community, and we can work together.
More at https://www.cybyr.com. Mark Fishburn, August 2022.
ExO Insight Newsletter
Join the newsletter to receive the latest updates in your inbox.









